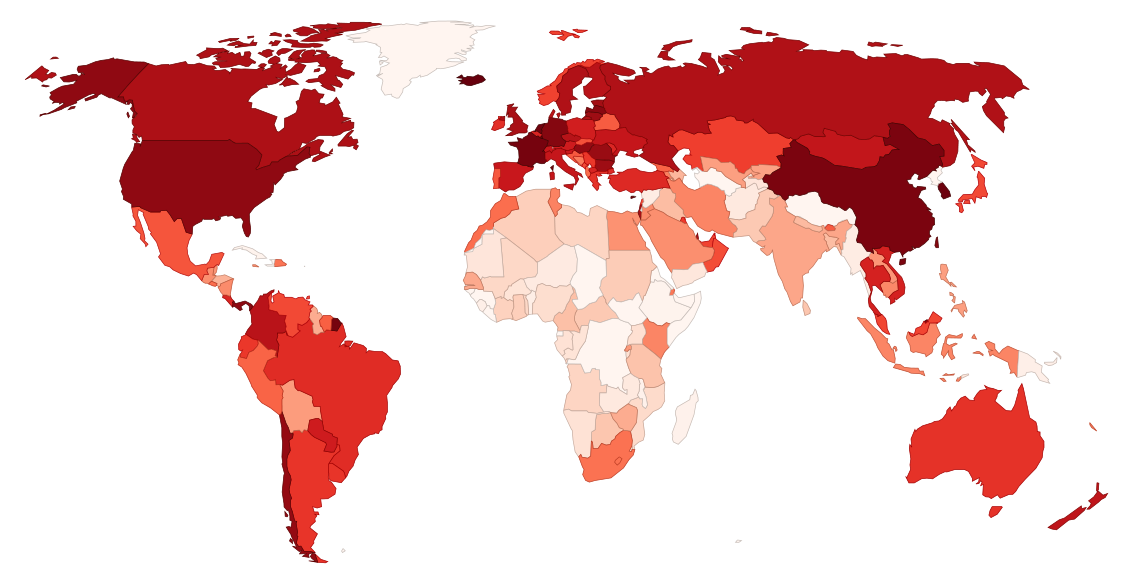
Two million attack reports from 5,000 hosts. See below for details.
what is this?
Fail2Ban is a free software package that watches a server's log files, looking for multiple failed login attempts and banning remote hosts that appear to be conducting brute-force password scans or searching for vulnerabilities. It also sends e-mail reports every time it bans a new host. But sometimes those reports go astray, and from them we can get an idea of who's attacking who, when, from where, and on what service.
From: MAILER-DAEMON@example.com To: fail2ban@mail.com Subject: failure notice Hi. This is the qmail-send program at example.com. I'm afraid I wasn't able to deliver your message to the following addresses. This is a permanent error; I've given up. Sorry it didn't work out. <you@mail.com>: Remote host said: 550 Requested action not taken: mailbox unavailable --- Below this line is a copy of the message. Return-Path: <fail2ban@mail.com> Subject: [Fail2Ban] SSH: banned 8.7.6.5 From: Fail2Ban <fail2ban@mail.com> To: you@mail.com Hi, The IP 8.7.6.5 has just been banned by Fail2Ban after 6 attempts against SSH. Regards, Fail2Ban
Fail2Ban is a pretty nice tool, and even when it doesn't help a lot with security (e.g., if you've turned off SSH password authentication), it still provides a drastic reduction in the logspam caused by intrusion attempts. The only problem I've seen with it is that, until July 2011, Fail2Ban's default configuration file specified the From: address fail2ban@mail.com and the To: address you@mail.com, which are both hosted by freemail provider Mail.com. I guess the person who set this up assumed that mail.com was invalid.
you@mail.com is either reserved or filled to the limit, so when Fail2Ban detects an attack on a misconfigured server, its report gets bounced back to the sender, fail2ban@mail.com. I registered that address back in 2010 so that the reports wouldn't fall into the wrong hands, and I left it to collect bounced reports. In July 2014, I parsed the reports and made the charts you see below. Unfortunately, Mail.com's "unlimited storage" is actually limited to 500,000 messages, which get used up in about a month, and I didn't download the reports very often, so there are some big gaps in the data.
ifaq
- Did you break into these computers to get their log files?
- No. All of the reports come from servers that were misconfigured and instructed to send messages to
fail2ban@mail.com. I just registered the account. - I have a great idea for some analysis/visualization you could do with this dataset.
- Cool. Send me an e-mail. My contact information is at https://int80k.com/~ken/.
- Can I get a copy of the data?
- I'm not going to release the raw data, as it may contain sensitive information about the structure of people's internal networks and services. I could generate an anonymized version (with country code, province, city, ASN, date and service type for each report) if people are interested. You can also check out the somewhat digested data used to make this page at fail2ban-data.json.
- How are you doing the IP → country and IP → ASN mapping?
- For country codes, I'm using MaxMind's GeoLite2 database. The IP → ASN map comes from the University of Oregon Route Views Archive Project, and the ASN names and country information come from CIDR Report.